Advanced Security For Business Libya

Yamamah, a leading system integrator in the Middle East and Africa region offers a wide range of advanced security solutions to secure critical enterprise assets and safeguard access to sensitive data in the most demanding datacenter environments. We offer security solutions to business verticals namely- Government, Banking & Finance, Telco, Oil & Gas, Education, Hospitality and Healthcare sectors. We support organizations to achieve and sustain compliance standards and optimally manage risk through full policy, procedure and controls lifecycle management.
Yamamah, today has on-the-ground sales and technical presence to execute large and complex projects and is completely geared up to provide turnkey security solutions. The security solutions we have in our portfolio are Cisco, Juniper, AppScan.
Email and Web Security Providers, Libya
The current generation has mastered the art of using internet which is a major reason for the web threat. Organizations today need a fresh approach to secure their networks from any kind of attacks by hackers or cybercriminals. Yamamah has partnered with companies like Cisco, Cyberoam and Juniper Networks to provide email and web security to its highly prestigious clientele.
Yamamah services are designed to monitor inbound and outbound traffic, block emails and websites with malicious content. Malware and other threats can cause data loss or degradation to your system. Our email and web security services include.
- Security Planning and Design Service.
- Email Security Configuration.
- Web Security Configuration.
- Security Optimization Service.
Benefits:
We help you mitigate risk and increase productivity with our Security solution services. Moreover, they are cost-effective; require no additional hardware or software and very little attention from the IT staff. We assist you in proactively identify and address risks. Protect against upcoming threats and plan for infrastructure changes.
Email Security Configuration
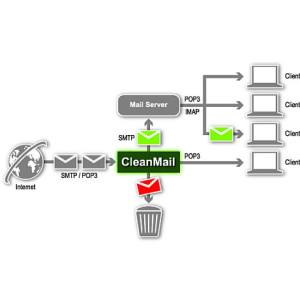 Yamamah offers email security configuration service to individuals and enterprise so that they reduce operating costs by improving ability to identify and mitigate vulnerabilities, anticipate resource and technical requirements, and effectively plan for infrastructure change
Yamamah offers email security configuration service to individuals and enterprise so that they reduce operating costs by improving ability to identify and mitigate vulnerabilities, anticipate resource and technical requirements, and effectively plan for infrastructure change
Our services also improve decision making and augment IT skill sets by using Cisco expertise to proactively identify and address vulnerabilities, to protect against emerging threats, and to plan enhancements to your security infrastructure.
Cisco Email Security Configuration
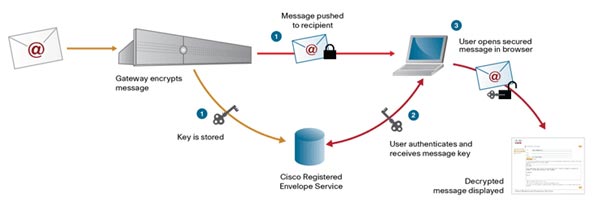 The Email Security Configuration and Installation Service provides limited configuration and installation assistance to make sure of effectiveness of antivirus (AV), antispam (AS), spyware, phishing as well as advice on industry best practices for email security.
The Email Security Configuration and Installation Service provides limited configuration and installation assistance to make sure of effectiveness of antivirus (AV), antispam (AS), spyware, phishing as well as advice on industry best practices for email security.
This service provides you with:
- Configuring data loss prevention (DLP)
- Message and content filtering features
- Lightweight Directory Access Protocol (LDAP) integration for incoming recipient validation and directory harvest attack prevention (DHAP)
Vulnerability Management
 Vulnerability management solutions protect the company applications, software and networks from attacks and threats. They allow the administrator to sense and remedy vulnerabilities with a powerful tool to manage risks as well as observe the quality of IT security. Did you know that organizations which effectively implement vulnerability management stay safe from data breaches and theft? Benefits of adopting this technology are numerous.
Vulnerability management solutions protect the company applications, software and networks from attacks and threats. They allow the administrator to sense and remedy vulnerabilities with a powerful tool to manage risks as well as observe the quality of IT security. Did you know that organizations which effectively implement vulnerability management stay safe from data breaches and theft? Benefits of adopting this technology are numerous.
Benefits
- Discover all the risks across the entire network
- Stay secure with complete end-to-end data encryption
- Integrated remediation and trouble-ticketing workflow
With vulnerability management techniques, IT threats are identified and evaluated. This assessment leads to process and detects vulnerabilities on time.
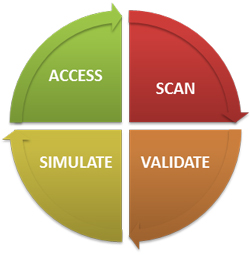
The process to identify threats and resolve them include:
- SCAN – Vulnerability management and security benchmarking
- VALIDATE – Vulnerability aggregation, penetration testing and validation
- SIMULATE – Layer-3 device vulnerability management
- ACCESS – Dynamic and static application vulnerability testing
Secure Mobility
 Employees today prefer to carry out most of the business communication and transactions through their personal smartphones, tablets and laptops to suit the mobile nature of their jobs due to client and company visits. With this trend growing exponentially, companies are in search of safest security policies and measures. Enabling the secure mobility technique will encourage broad use of mobile computing in businesses.
Employees today prefer to carry out most of the business communication and transactions through their personal smartphones, tablets and laptops to suit the mobile nature of their jobs due to client and company visits. With this trend growing exponentially, companies are in search of safest security policies and measures. Enabling the secure mobility technique will encourage broad use of mobile computing in businesses.
Secure Mobility enables businesses to put into effect their company data governance policies at the user level. This assists each user in understanding which data should be classified as sensitive. Appropriate measures can be taken so that your sensitive data cannot be maliciously or mistakenly leaked.
Yamamah, with the best and effective secure mobility solutions, guarantees that your organization’s mobility management meets today’s security needs.
Key Benefits
- Immediately boost the productivity of the mobile users
- Reduce the network maintenance and communication costs
- Improvement in the overall organizational responsiveness
- Well supports the overall unified communications program
As the most valuable sensitive data needs to be accessible to the mission critical workforce, round the clock online, as well as offline, the portability is extremely crucial. Hence the secure information sharing may not be completed without the ability for trusted users to securely transport data and their entire workspace environment. The best way to share your sensitive data is by classifying the data, secure the information to be shared, transfer and move them through encrypted and biometric USB’s.
Vulnerability Management
 Vulnerability management solutions protect the company applications, software and networks from attacks and threats. They allow the administrator to sense and remedy vulnerabilities with a powerful tool to manage risks as well as observe the quality of IT security. Did you know that organizations which effectively implement vulnerability management stay safe from data breaches and theft? Benefits of adopting this technology are numerous.
Vulnerability management solutions protect the company applications, software and networks from attacks and threats. They allow the administrator to sense and remedy vulnerabilities with a powerful tool to manage risks as well as observe the quality of IT security. Did you know that organizations which effectively implement vulnerability management stay safe from data breaches and theft? Benefits of adopting this technology are numerous.
Benefits
- Discover all the risks across the entire network
- Stay secure with complete end-to-end data encryption
- Integrated remediation and trouble-ticketing workflow
With vulnerability management techniques, IT threats are identified and evaluated. This assessment leads to process and detects vulnerabilities on time.
The process to identify threats and resolve them include:
- SCAN – Vulnerability management and security benchmarking
- VALIDATE – Vulnerability aggregation, penetration testing and validation
- SIMULATE – Layer-3 device vulnerability management
- ACCESS – Dynamic and static application vulnerability testing
Secure Mobility
 Employees today prefer to carry out most of the business communication and transactions through their personal smartphones, tablets and laptops to suit the mobile nature of their jobs due to client and company visits. With this trend growing exponentially, companies are in search of safest security policies and measures. Enabling the secure mobility technique will encourage broad use of mobile computing in businesses.
Employees today prefer to carry out most of the business communication and transactions through their personal smartphones, tablets and laptops to suit the mobile nature of their jobs due to client and company visits. With this trend growing exponentially, companies are in search of safest security policies and measures. Enabling the secure mobility technique will encourage broad use of mobile computing in businesses.
Secure Mobility enables businesses to put into effect their company data governance policies at the user level. This assists each user in understanding which data should be classified as sensitive. Appropriate measures can be taken so that your sensitive data cannot be maliciously or mistakenly leaked.
Yamamah, with the best and effective secure mobility solutions, guarantees that your organization’s mobility management meets today’s security needs.
Key Benefits
- Immediately boost the productivity of the mobile users
- Reduce the network maintenance and communication costs
- Improvement in the overall organizational responsiveness
- Well supports the overall unified communications program
As the most valuable sensitive data needs to be accessible to the mission critical workforce, round the clock online, as well as offline, the portability is extremely crucial. Hence the secure information sharing may not be completed without the ability for trusted users to securely transport data and their entire workspace environment. The best way to share your sensitive data is by classifying the data, secure the information to be shared, transfer and move them through encrypted and biometric USB’s.
Access Control
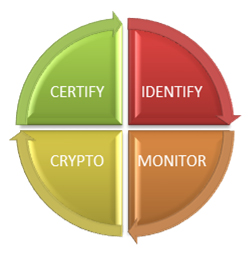 In this advanced technological world, the access control systems have already proved its value by efficiently functioning for security purpose. These advanced systems allow access to the sensitive data only to the authorized users by providing comprehensive real-time visibility into all activity. In addition, the encryption mechanisms guarantee that sensitive data will not be accessed by unauthorized users even if it inadvertently falls into the wrong hands. With the perfect access control software, regardless of your business size, it provides you the real time visibility in to the present risk position.
In this advanced technological world, the access control systems have already proved its value by efficiently functioning for security purpose. These advanced systems allow access to the sensitive data only to the authorized users by providing comprehensive real-time visibility into all activity. In addition, the encryption mechanisms guarantee that sensitive data will not be accessed by unauthorized users even if it inadvertently falls into the wrong hands. With the perfect access control software, regardless of your business size, it provides you the real time visibility in to the present risk position.
The process followed is to:
- IDENTIFY – IT & system management, network and data security
- MONITOR – Real time database security, Auditing and monitoring
- CRYPTO – Multi-factor authentication, HSMs and data encryption
- CERTIFY – Enterprise certificate management and audio provisioning
The process allows you to confidently manage and reduce unauthorized access, fraud and cost of compliance across your organization as well as from other dangerous attacks.
Key Benefits:
- Allows authorized users to access sensitive data
- Embed fulfillment checks and mandatory risk mitigation into business processes
- Excellent data security
- Reduced costs and bills


 Advanced Security For Business Libya
Advanced Security For Business Libya






 Yamamah offers email security configuration service to individuals and enterprise so that they reduce operating costs by improving ability to identify and mitigate vulnerabilities, anticipate resource and technical requirements, and effectively plan for infrastructure change
Yamamah offers email security configuration service to individuals and enterprise so that they reduce operating costs by improving ability to identify and mitigate vulnerabilities, anticipate resource and technical requirements, and effectively plan for infrastructure change The Email Security Configuration and Installation Service provides limited configuration and installation assistance to make sure of effectiveness of antivirus (AV), antispam (AS), spyware, phishing as well as advice on industry best practices for email security.
The Email Security Configuration and Installation Service provides limited configuration and installation assistance to make sure of effectiveness of antivirus (AV), antispam (AS), spyware, phishing as well as advice on industry best practices for email security. Vulnerability management solutions protect the company applications, software and networks from attacks and threats. They allow the administrator to sense and remedy vulnerabilities with a powerful tool to manage risks as well as observe the quality of IT security. Did you know that organizations which effectively implement vulnerability management stay safe from data breaches and theft? Benefits of adopting this technology are numerous.
Vulnerability management solutions protect the company applications, software and networks from attacks and threats. They allow the administrator to sense and remedy vulnerabilities with a powerful tool to manage risks as well as observe the quality of IT security. Did you know that organizations which effectively implement vulnerability management stay safe from data breaches and theft? Benefits of adopting this technology are numerous. Employees today prefer to carry out most of the business communication and transactions through their personal smartphones, tablets and laptops to suit the mobile nature of their jobs due to client and company visits. With this trend growing exponentially, companies are in search of safest security policies and measures. Enabling the secure mobility technique will encourage broad use of mobile computing in businesses.
Employees today prefer to carry out most of the business communication and transactions through their personal smartphones, tablets and laptops to suit the mobile nature of their jobs due to client and company visits. With this trend growing exponentially, companies are in search of safest security policies and measures. Enabling the secure mobility technique will encourage broad use of mobile computing in businesses. In this advanced technological world, the access control systems have already proved its value by efficiently functioning for security purpose. These advanced systems allow access to the sensitive data only to the authorized users by providing comprehensive real-time visibility into all activity. In addition, the encryption mechanisms guarantee that sensitive data will not be accessed by unauthorized users even if it inadvertently falls into the wrong hands. With the perfect access control software, regardless of your business size, it provides you the real time visibility in to the present risk position.
In this advanced technological world, the access control systems have already proved its value by efficiently functioning for security purpose. These advanced systems allow access to the sensitive data only to the authorized users by providing comprehensive real-time visibility into all activity. In addition, the encryption mechanisms guarantee that sensitive data will not be accessed by unauthorized users even if it inadvertently falls into the wrong hands. With the perfect access control software, regardless of your business size, it provides you the real time visibility in to the present risk position.